Recently, it was revealed that the Linux kernel has a TCP "SACK PANIC" remote denial of service vulnerability (vulnerability number: CVE-2019-11477,CVE-2019-11478,CVE-2019-11479), an attacker can use this vulnerability to remotely attack the target server, causing the system to crash or be unable to provide services. Many cloud service vendors have released this information and provided repair methods. It is recommended that everyone update it in time.
【Vulnerability details】
Jonathan Looney, a researcher on the Netflix information security team, discovered that there is a serious remote DoS vulnerability in the kernel of Linux and FreeBSD systems. Attackers can use this vulnerability to construct and send specific SACK A sequence of requests to the target server causes a server crash or denial of service.
[Risk Level]
Higher
[Vulnerability Risk]
Remotely send specially constructed attack packets, causing the target Linux or FreeBSD server to crash or service is not available.
[Affected versions]
The currently known affected versions are as follows:
FreeBSD 12 (uses RACK TCP protocol stack)
CentOS 5 (Redhat official has stopped supporting it, no Patches will be provided again)
CentOS 6
CentOS 7
Ubuntu 18.04 LTS
Ubuntu 16.04 LTS
Ubuntu 19.04
Ubuntu 18.10
[Repair method]
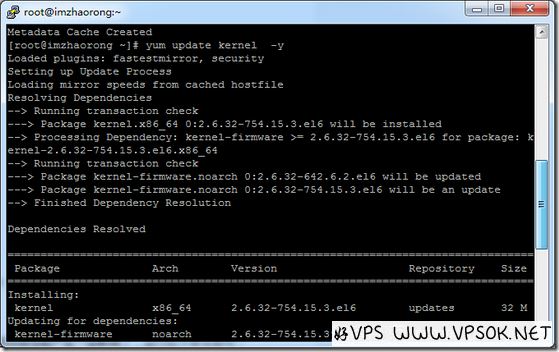
1. CentOS 6/7 series
1) yum clean all && yum makecache, update the software source;
2) yum update kernel -y, update the current kernel version;
3) reboot, restart the system after the update to take effect;
4) uname -a, check whether the current version is the safe version provided below, if so, the repair is successful.
2. Ubuntu 16.04/18.04 LTS series
1) sudo apt-get update && sudo apt-get install linux-image-generic, update the software source and Install the latest kernel version;
2) sudo reboot, restart the system after the update to take effect;
3) uname -a, check whether the current version is the safe version provided below, if so, the repair is successful.
3. Temporary mitigation plan
If it is inconvenient to restart the kernel patch update, you can choose the following method to disable the kernel SACK configuration to prevent vulnerability exploitation (which may have a certain impact on network performance), and run the following command:
1) echo ""net.ipv4.tcp_sack = 0"" >> /etc/sysctl.conf, disable SACK configuration;
2) sysctl -p, reload the configuration to make it effective.
[Security version]
The detailed kernel repair versions of major Linux distribution manufacturers are as follows:
CentOS 6: 2.6.32-754.15.3
CentOS 7: 3.10.0- 957.21.3
Ubuntu 18.04 LTS: 4.15.0-52.56
Ubuntu 16.04 LTS: 4.4.0-151.178
postid
9140
